Computers & Laptops | June 3, 2023

Lowering your guard in cybersecurity is one of the mistakes that an average user should never make. News about the emergence of new ways to infect computers are frequent, and when facing threats like QBot, it is crucial to be cautious. This dangerous virus uses a popular Windows tool to infect PCs without users being aware that it has taken hold in their systems.
Specifically, the application that this malware utilizes is the popular WordPad in its Windows 10 and later versions, which many users use for quick note-taking without the need for Word or any other equivalent application. The QBot virus, also known as Qakbot, takes advantage of this legitimate program to go unnoticed and avoid triggering antivirus software by executing DLL-based attacks on the infected computer.
The pathway through which the QBot malware reaches computers is through phishing emails, where it disguises itself as a seemingly trustworthy sender. This virus arrives within a compressed ZIP file, which less cautious users end up downloading. Upon opening it, an .EXE file and the malicious version of the accompanying DLL file called edputil.dll appear.
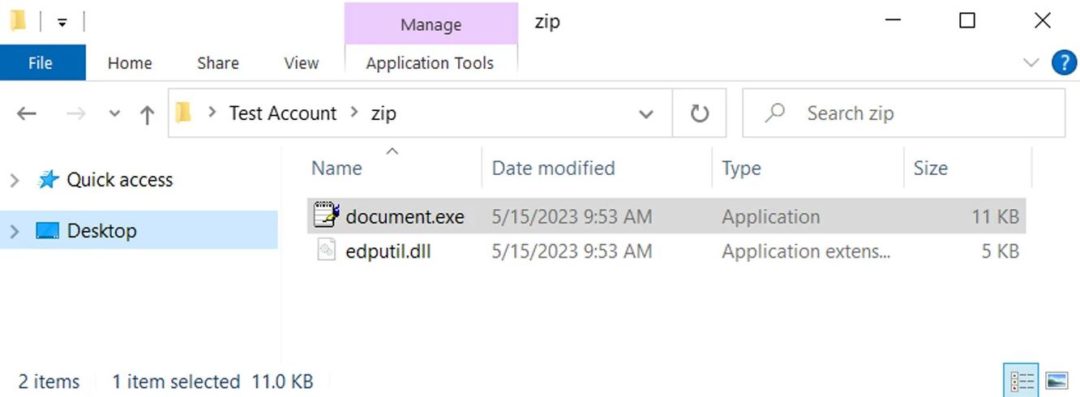
Upon opening it, the QBot virus will start running in the background, having bypassed the security filters and the user’s own precautions. Once in the system, it can acquire new email addresses to continue its phishing attacks, aiming to obtain personal or corporate information that it can hold hostage for ransom.
The danger of QBot is not limited to this form of attack and data hijacking; it can also manifest in other ways. In any case, whenever you receive an email with attachments, it is important to ensure that the source is trustworthy and not assume that they are free of viruses. Always analyze the contents of attachments with an appropriately updated antivirus program.